Most of our personal and financial information is hidden behind just a username and password, the importance of keeping this data secure is very high.
For the convenience of storing and entering passwords to websites, there are password managers, they can be both local and cloud.
Today we are going to show you how to install your own password manager on your virtual server.
Installing the Vaultwarden
To install Vaultwarden, we need to set up a Docker server, a domain name that will be pointed to your server, and an SSL certificate. You can point the domain name to Cloudflare and use their SSL certificate. You can learn more about how to install Docker in this article.
To install Vaultwarden, we only need to run one command
docker run -d --name vaultwarden -v /vw-data/:/data/ -p 80:80 vaultwarden/server:latestIn this command, replace the path /vw-data/ with your own, in this directory will be saved files needed to run Vaultwarden.
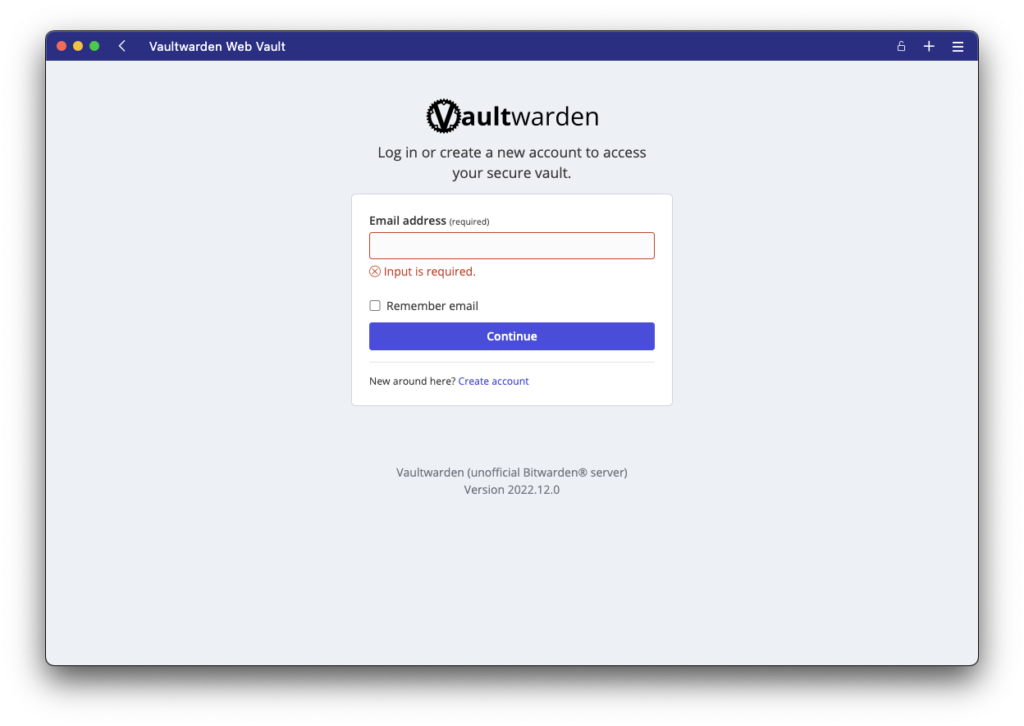
Once the container installation is complete, you can go to the address of your server’s domain name and you will be taken to the Vaultwarden login page.
Vaultwarden and HTTPS
For Vaultwarden to work correctly, you need to have a ssl certificate configured on the domain name, for example you can use Cloudflare and just point your domain name to the server, or configure a reverse proxy.
One of the easiest ways is to use Caddy’s reverse proxy. To deploy Vaultwarden and Caddy immediately, create a docker-compose.yaml file and put the following data into it
version: '3'
services:
vaultwarden:
image: vaultwarden/server:latest
container_name: vaultwarden
restart: always
environment:
WEBSOCKET_ENABLED: "true" # Enable WebSocket notifications.
volumes:
- ./vw-data:/data
caddy:
image: caddy:2
container_name: caddy
restart: always
ports:
- 80:80 # Needed for the ACME HTTP-01 challenge.
- 443:443
volumes:
- ./Caddyfile:/etc/caddy/Caddyfile:ro
- ./caddy-config:/config
- ./caddy-data:/data
environment:
DOMAIN: "https://vaul.domain.com" # Your domain.
EMAIL: "[email protected]" # The email address to use for ACME registration.
LOG_FILE: "/data/access.log"В этой же директории создадим файл Caddyfile в который мы внесем следующие данные
{$DOMAIN}:443 {
log {
level INFO
output file {$LOG_FILE} {
roll_size 10MB
roll_keep 10
}
}
# Use the ACME HTTP-01 challenge to get a cert for the configured domain.
tls {$EMAIL}
# This setting may have compatibility issues with some browsers
# (e.g., attachment downloading on Firefox). Try disabling this
# if you encounter issues.
encode gzip
# Notifications redirected to the WebSocket server
reverse_proxy /notifications/hub vaultwarden:3012
# Proxy everything else to Rocket
reverse_proxy vaultwarden:80 {
# Send the true remote IP to Rocket, so that vaultwarden can put this in the
# log, so that fail2ban can ban the correct IP.
header_up X-Real-IP {remote_host}
}
}If you want to run Vaultwarden on a local network for a local domain name, the Caddyfile will look like this
domain.local:443 {
reverse_proxy vaultwarden:80
tls internal
}Creating a user in Vaultwarden
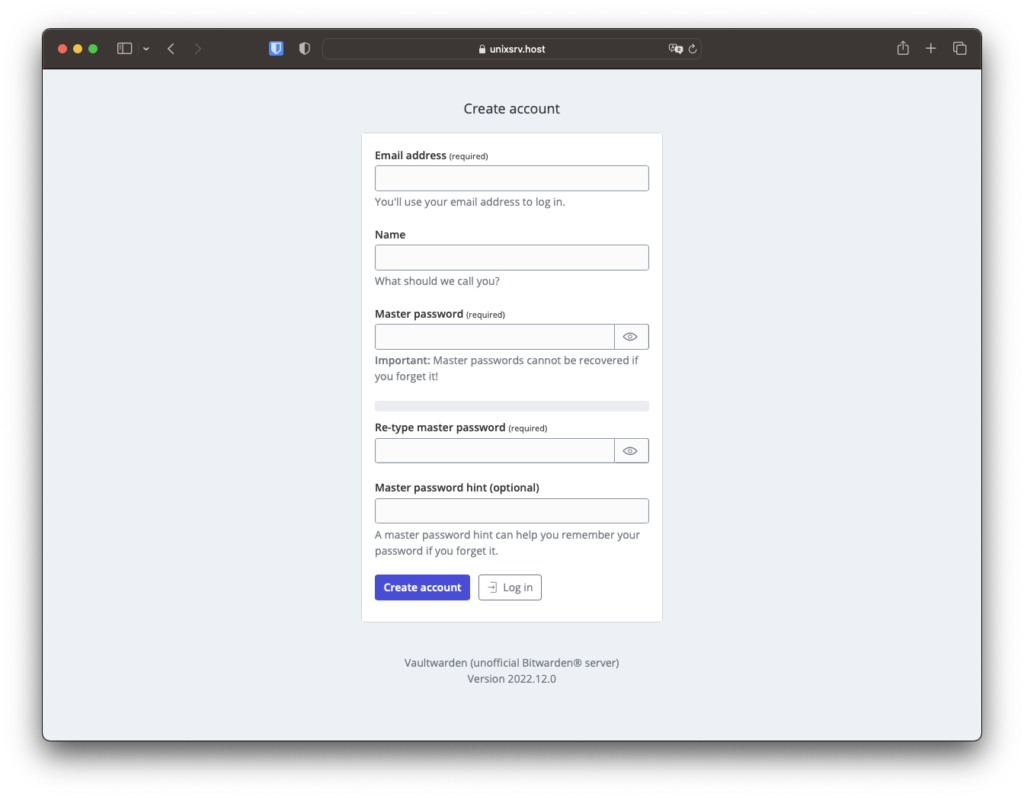
To create a new account, click Create account at the bottom under the Continue button.
This completes the installation of Vaultwarden. You can use the Bitwarden extension for your browser or desktop, in the settings you will need to specify the domain name where Vaultwarden is available.
